On Thursday 9th December, security researchers found a new zero-day vulnerability in the Apache Log4j Java library. The vulnerability, which enables attackers to gain full control of affected servers, is easy to exploit and is indeed already being exploited in the wild.
Although the vulnerability was first discovered in video game Minecraft, any systems and services that use the Java logging library, Apache Log4j between versions 2.0 and 2.14.1 are affected and at risk. Fortunately, neither the Webgains platform nor tech stack are under threat; our affiliate marketing network doesn’t make use of Log4j and Webgains isn’t built on Java or Java libraries.
Neither the Webgains platform nor tech stack are under threat; our affiliate marketing network doesn’t make use of Log4j and Webgains isn’t built on Java or Java libraries.
What is a Zero-Day vulnerability?
A zero-day exploit is an exploit that is unknown by the vendor of software and is used before it is patched.
More about Log4j
Log4j is an open-source Java-based logging tool available from Apache, used to log error messages in applications. It will interpret a log message as a URL, go and fetch it, and even execute any executable payload it contains with the full privileges of the main program. It’s widely used across many Java applications and infrastructure.
Log4j runs in many libraries including Struts 2, Solr, Druid, Flink and Swift frameworks, and is used in many enterprise-level software applications across the world including systems used by Azure, Dell and Amazon to name a few. The sheer volume of devices at risk combined with the ease with which they can be exploited, means that this vulnerability must be taken extremely seriously in both public and private sectors.
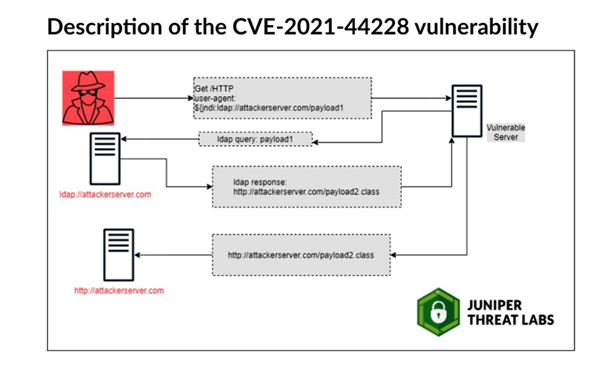
Please refer to Juniper Threat Labs diagram below to understand this Log4j vulnerability, tracked as CVE-2021-44228.
What happens now?
The central advice coming from US federal body CISA at this moment is to identify internet-facing devices running Log4j and upgrade them to version 2.15.0, or to apply the mitigations provided by vendors “immediately”. But it also recommends setting up alerts for probes or attacks on devices running Log4j.
Apache has already released a security patch that disables the system that can be exploited, and this update is now being deployed across all companies that maintain and host this software.

